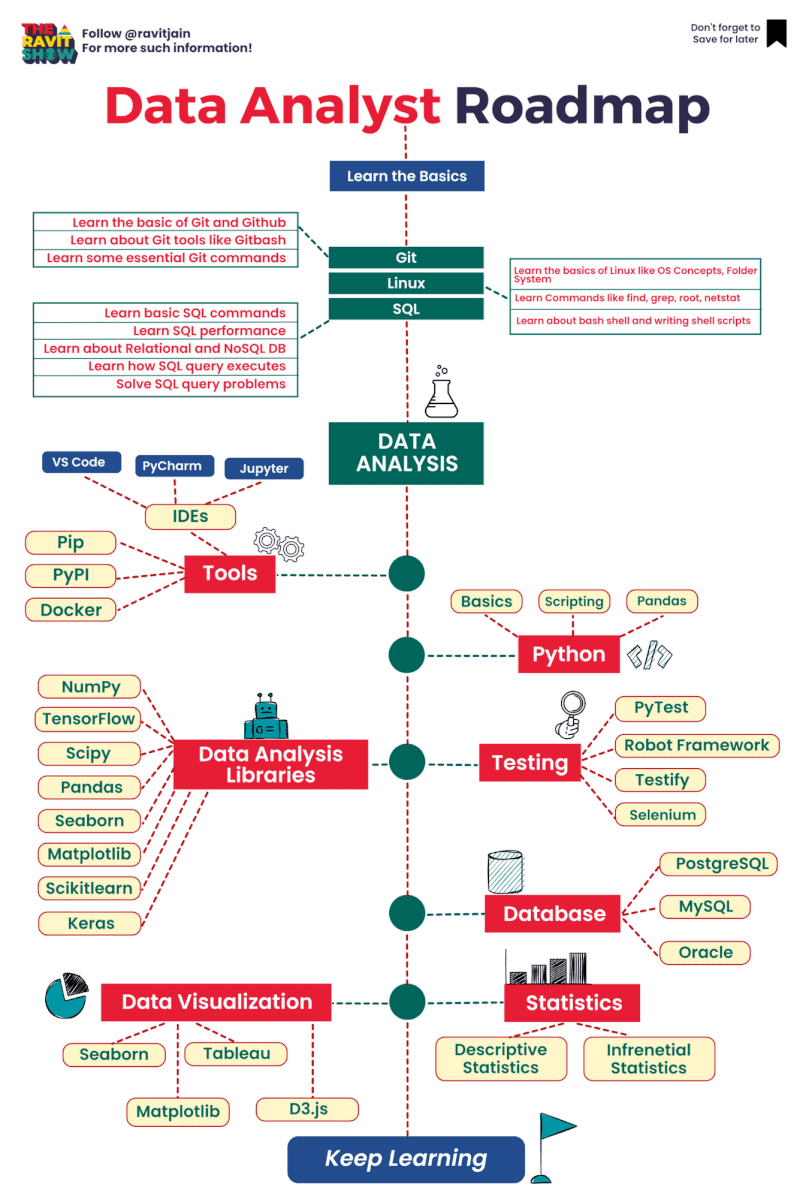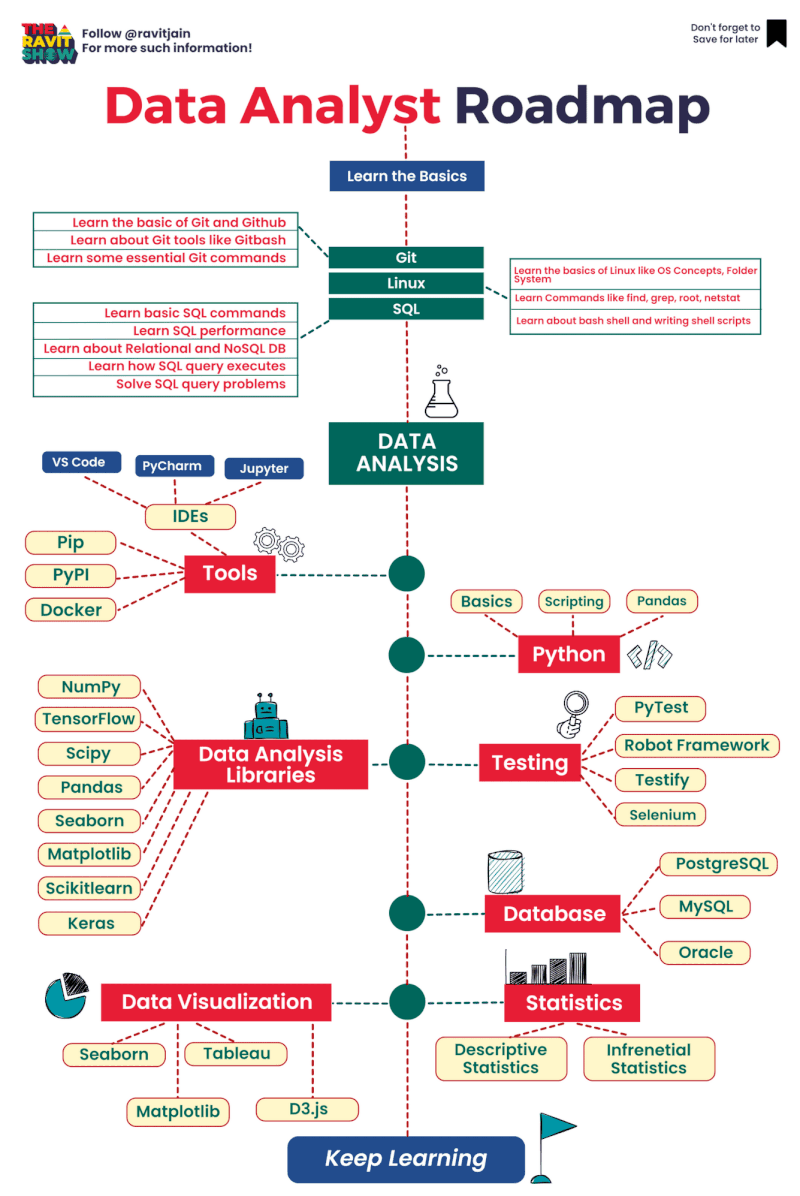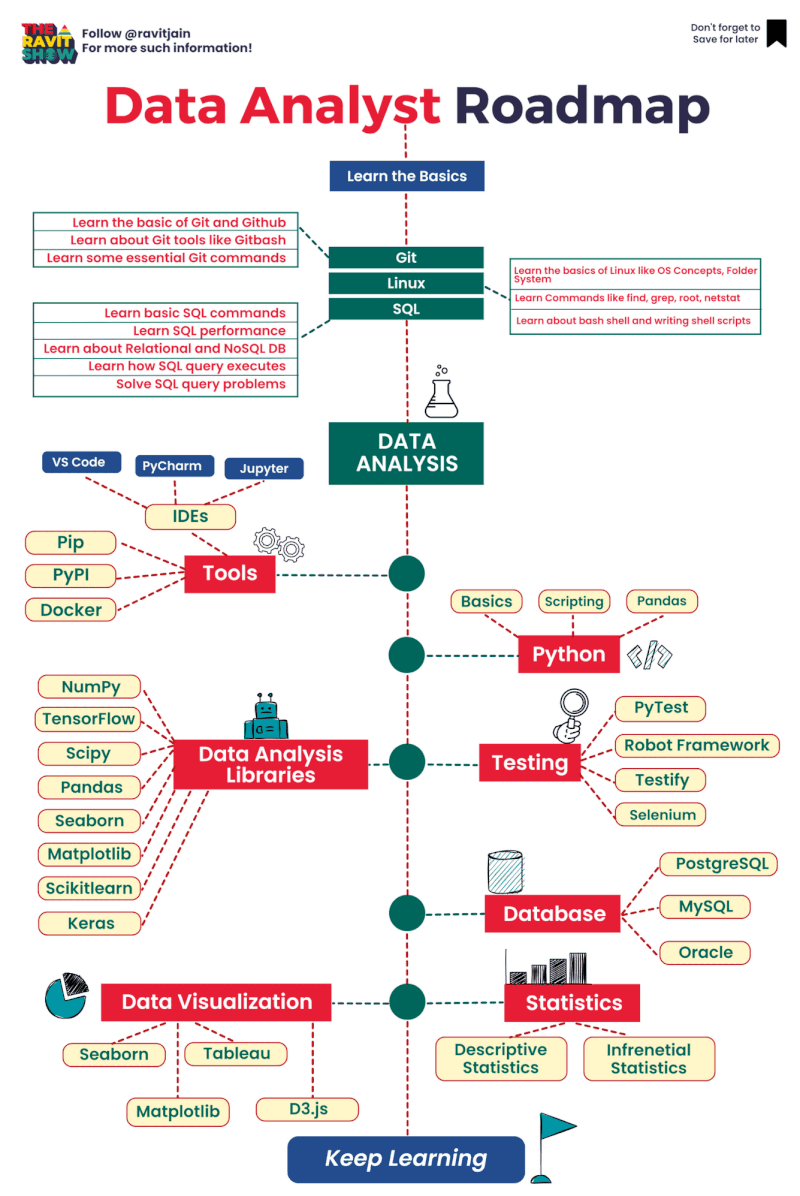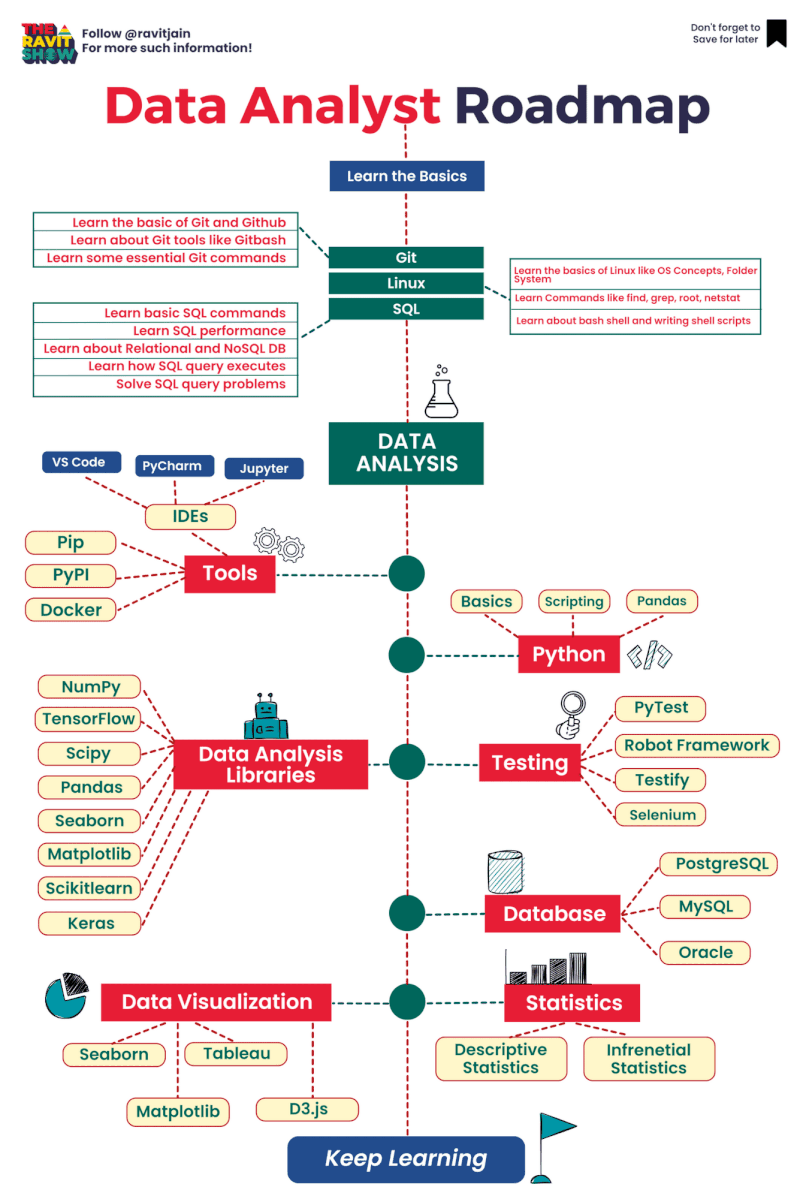
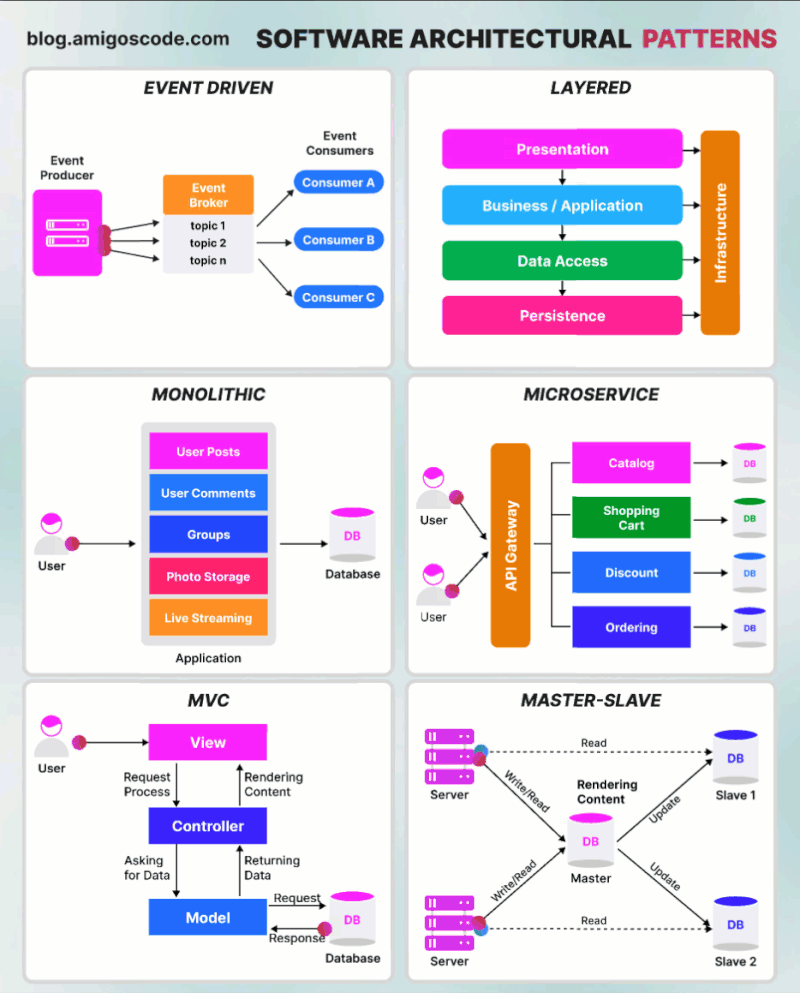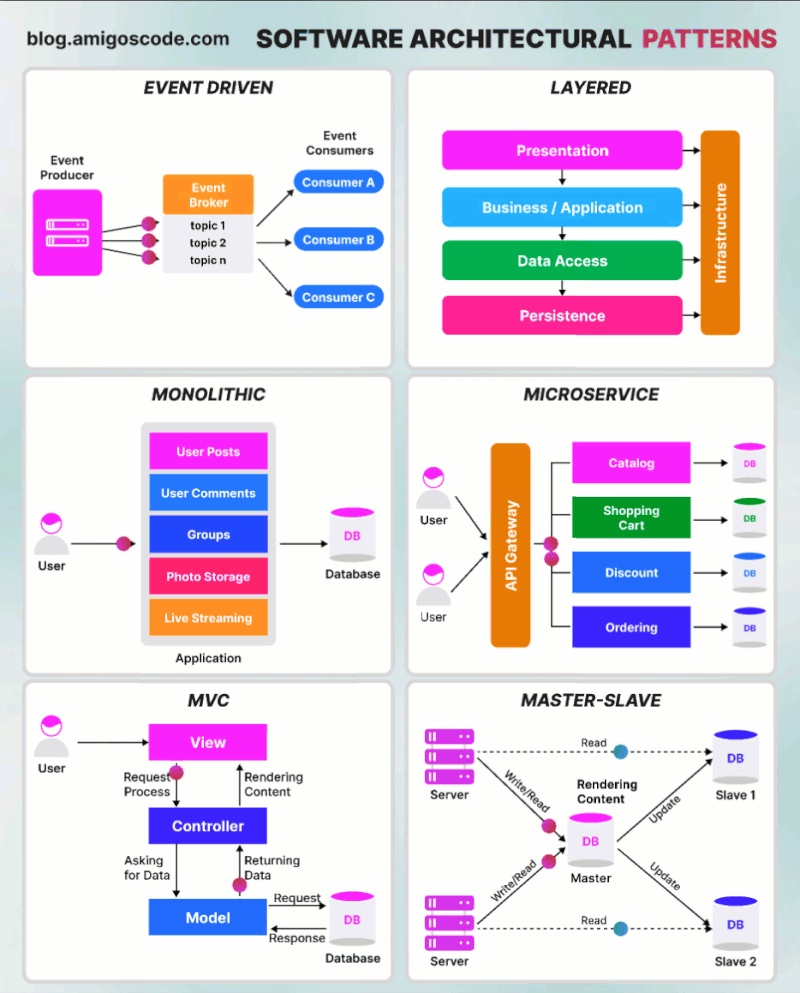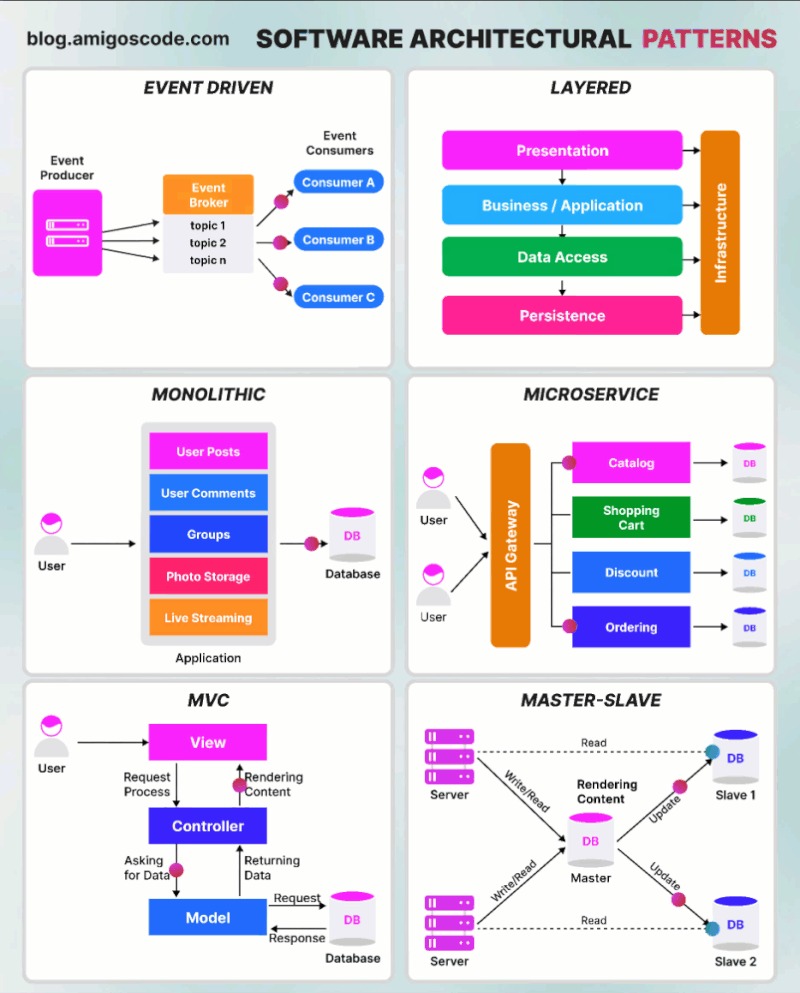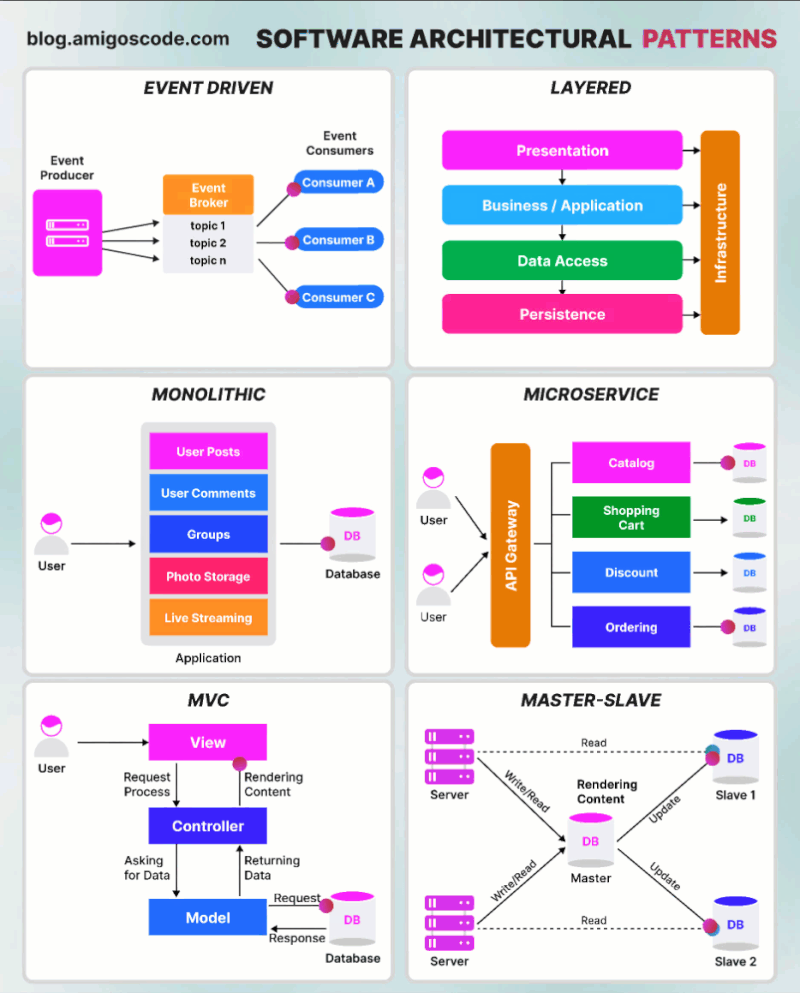
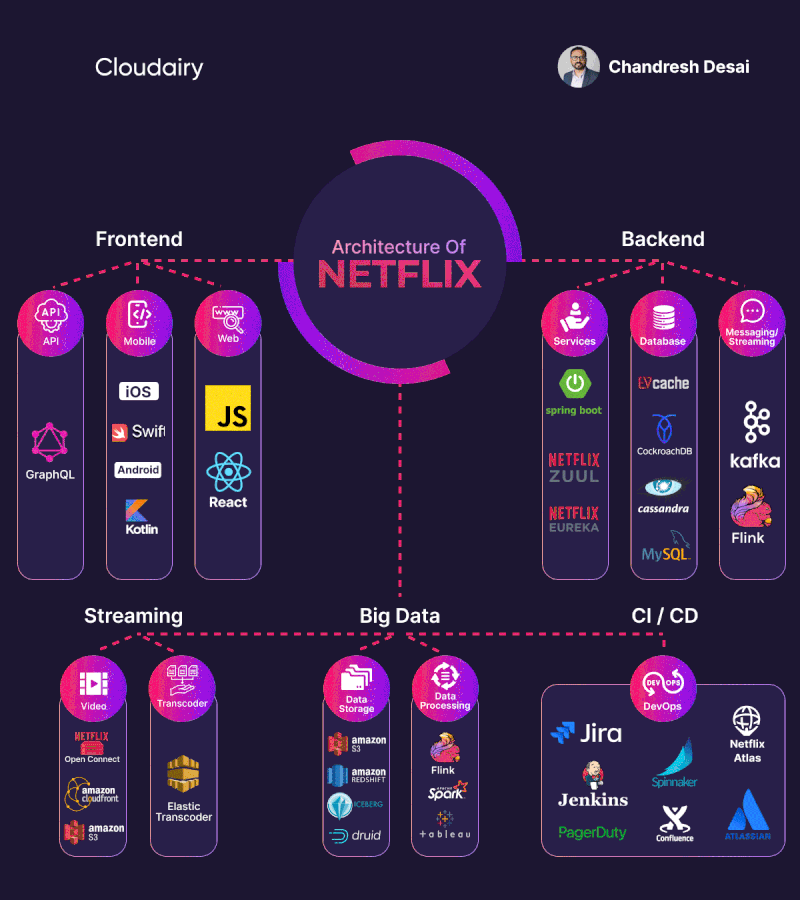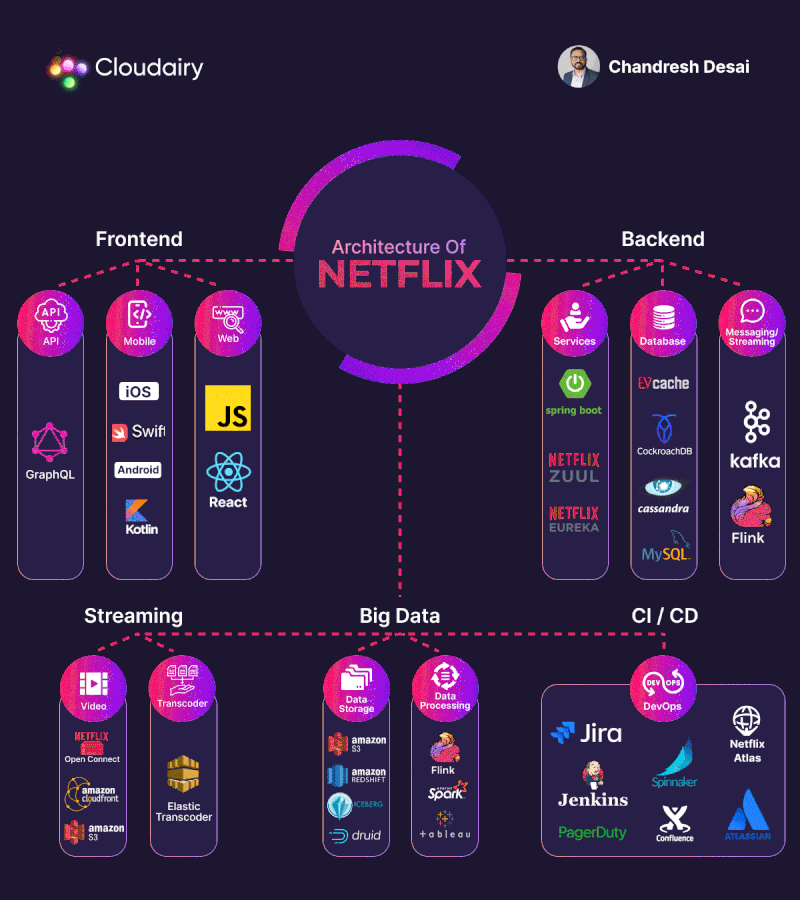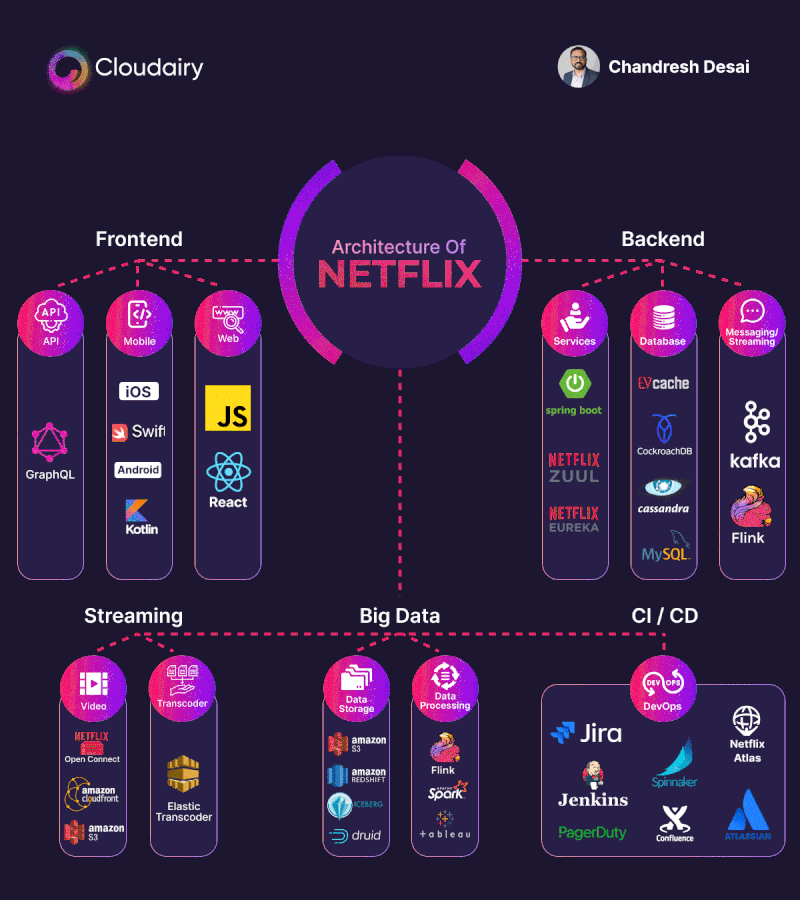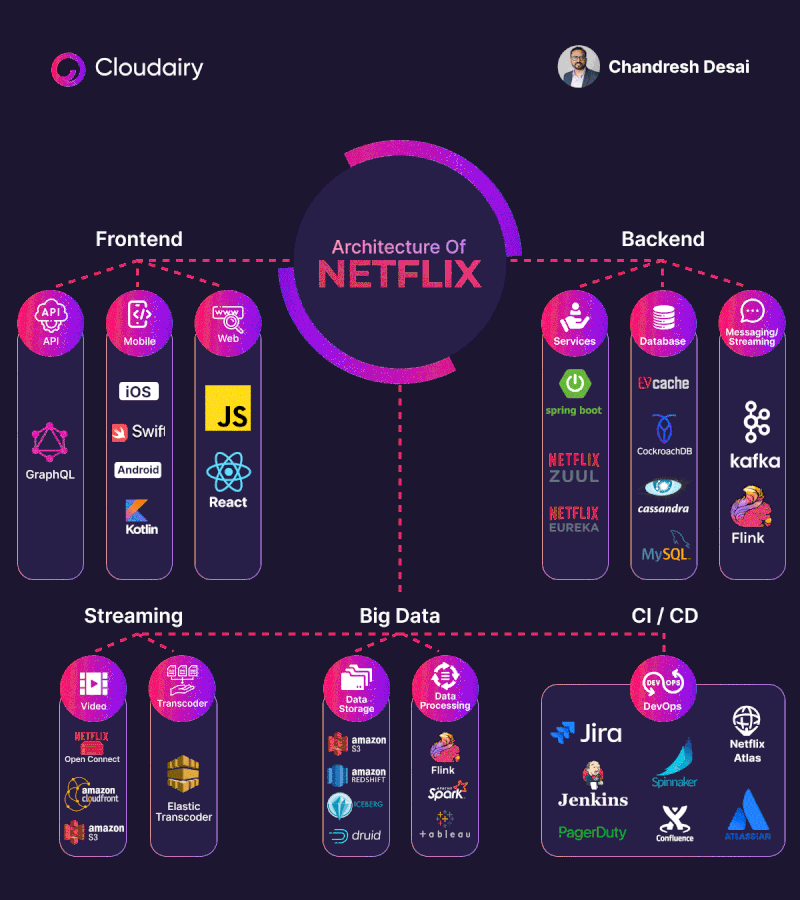
Basic authentication Apache
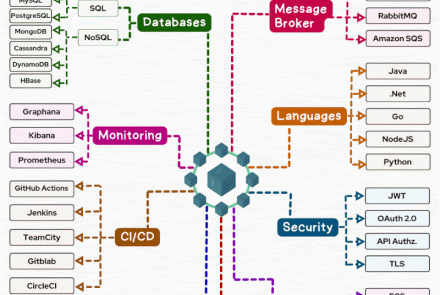
Cấu hình Firewalld cho phép dịch vụ http ( để các máy Client có thể truy cập ) :
firewall-cmd --zone=public --permanent --add-service=http
firewall-cmd --reload
Tạo user truy nhập httpd bằng lệnh htpasswd :
htpasswd -c /etc/httpd/conf/passwords admin
New password :
Re-type new password :
Options :
c: tùy chọn tạo 1 file mới chứa thông tin user ( file/etc/httpd/conf/passwords)admin: tên user
Tạo file cấu hình auth_basic.conf :
vi /etc/httpd/conf.d/auth_basic.conf
Thêm vào nội dung sau :
<Directory /var/www/html/>
AuthType Basic
AuthName "Basic Authentication"
AuthUserFile /etc/httpd/conf/passwords
Require valid-user
</Directory>
Khởi động lại dịch vụ httpd :
sudo systemctl restart httpd
Trên Client truy cập vào Web Server Apache trên trình duyệt
Nhập user và password vừa tạo
Ubuntu:
sudo htpasswd -c /etc/apache2/.htpasswd sammy
If we view the contents of the file, we can see the username and the encrypted password for each record:
cat /etc/apache2/.htpasswd
Output
sammy:$apr1$.0CAabqX$rb8lueIORA/p8UzGPYtGs/
another_user:$apr1$fqH7UG8a$SrUxurp/Atfq6j7GL/VEC1
Option 1: Configuring Access Control within the Virtual Host Definition (Preferred)
sudo nano /etc/apache2/sites-enabled/000-default.conf
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
Authentication is done on a per-directory basis. To set up authentication, you will need to target the directory you wish to restrict with a <Directory ___> block. In our example, we’ll restrict the entire document root, but you can modify this listing to only target a specific directory within the web space:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
<Directory "/var/www/html">
</Directory>
</VirtualHost>
Within this directory block, specify that we wish to set up Basic authentication. For the AuthName, choose a realm name that will be displayed to the user when prompting for credentials. Use the AuthUserFile directive to point Apache to the password file we created. Finally, we will require a valid-user to access this resource, which means anyone who can verify their identity with a password will be allowed in:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
<Directory "/var/www/html">
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
</Directory>
</VirtualHost>
Save and close the file when you are finished.
Before restarting the web server, you can check the configuration with the following command:
sudo apache2ctl configtest
sudo systemctl restart apache2
sudo systemctl status apache2
Option 2: Configuring Access Control with .htaccess Files
To enable password protection using .htaccess files, open the main Apache configuration file:
sudo nano /etc/apache2/apache2.conf
Find the <Directory> block for the /var/www directory that holds the document root. Turn on .htaccess processing by changing the AllowOverride directive within that block from “None” to “All”:
File: /etc/apache2/apache2.conf
. . .
<Directory /var/www/>
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
. . .
Save and close the file when you are finished.
Next, we need to add an .htaccess file to the directory we wish to restrict. In our demonstration, we’ll restrict the entire document root (the entire website) which is based at /var/www/html, but you can place this file in any directory where you wish to restrict access:
sudo nano /var/www/html/.htaccess
Within this file, specify that we wish to set up Basic authentication. For the AuthName, choose a realm name that will be displayed to the user when prompting for credentials. Use the AuthUserFile directive to point Apache to the password file we created. Finally, we will require a valid-user to access this resource, which means anyone who can verify their identity with a password will be allowed in:
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
sudo systemctl restart apache2
sudo systemctl status apache2