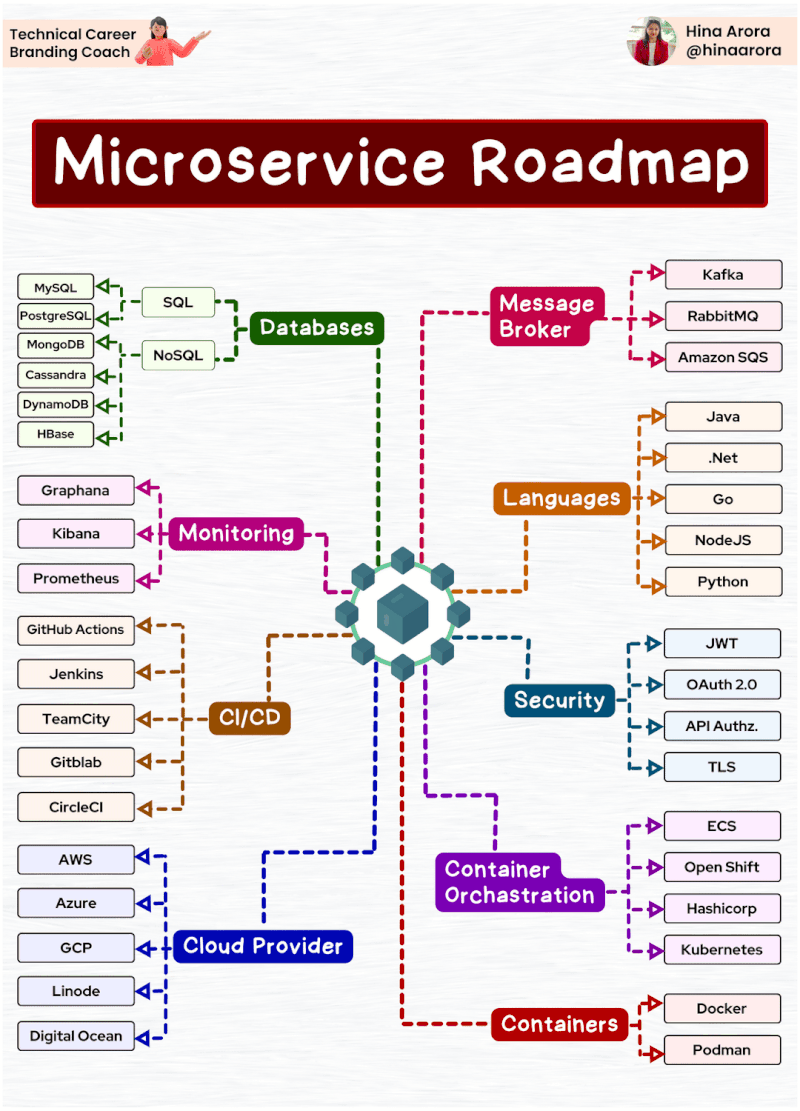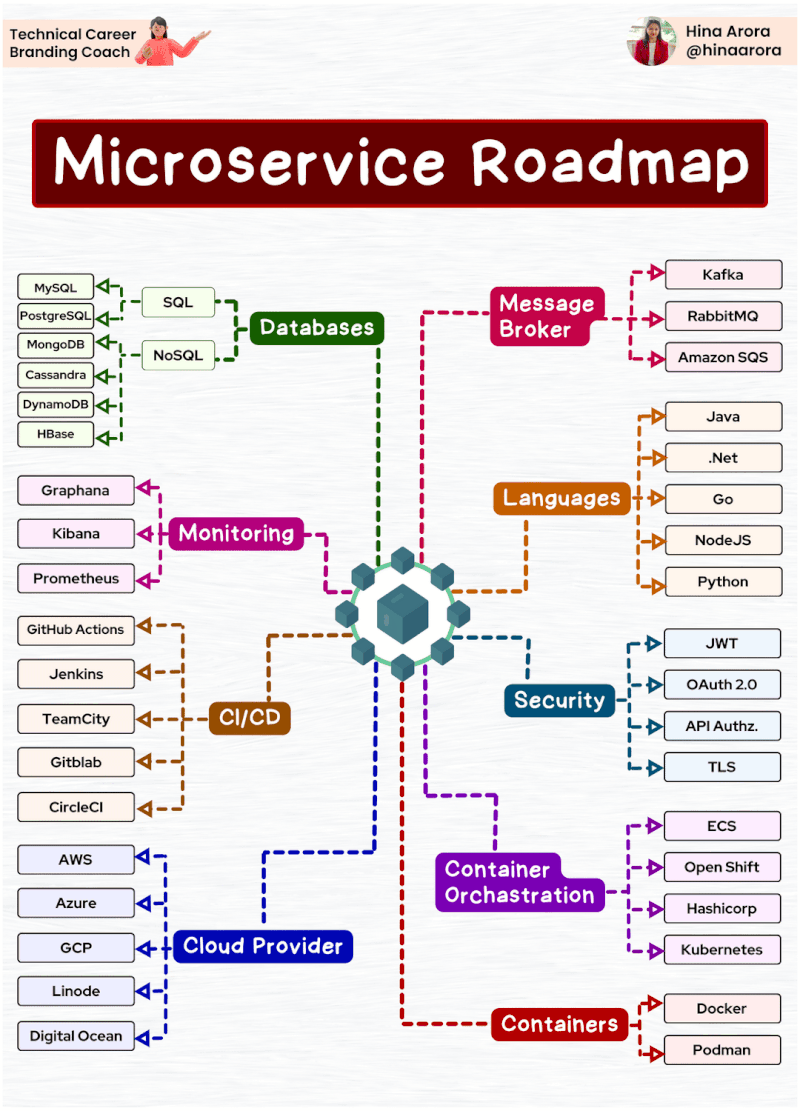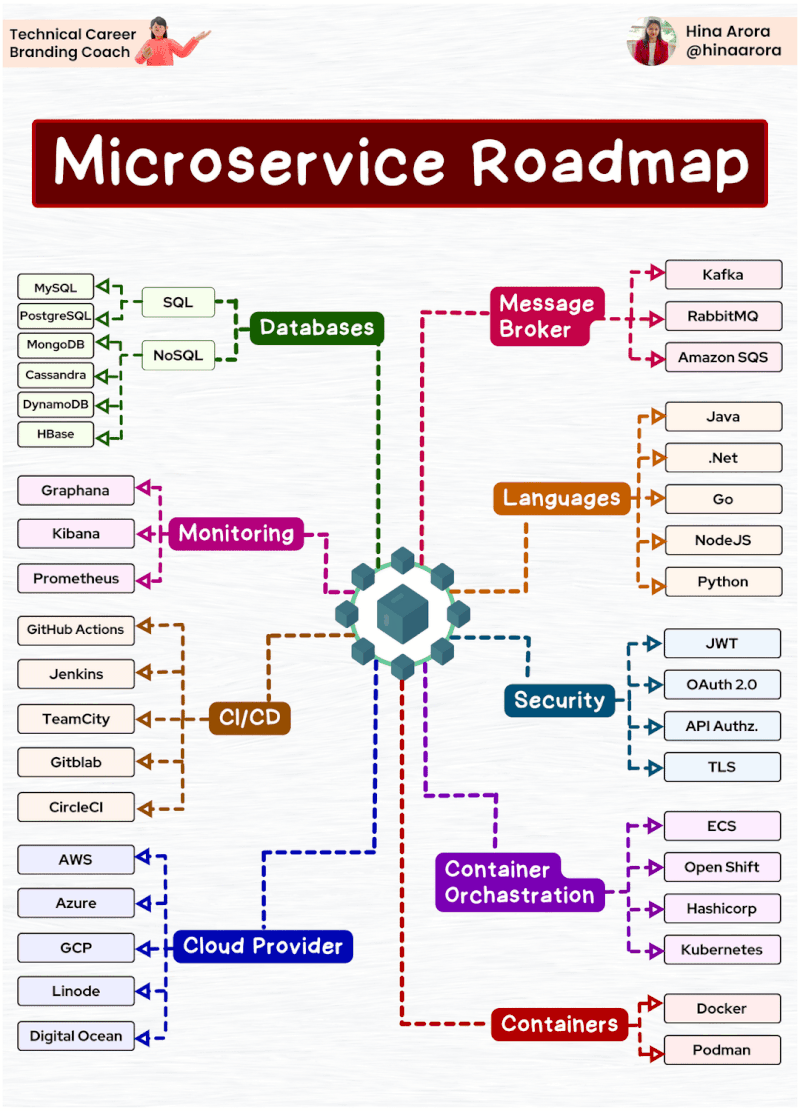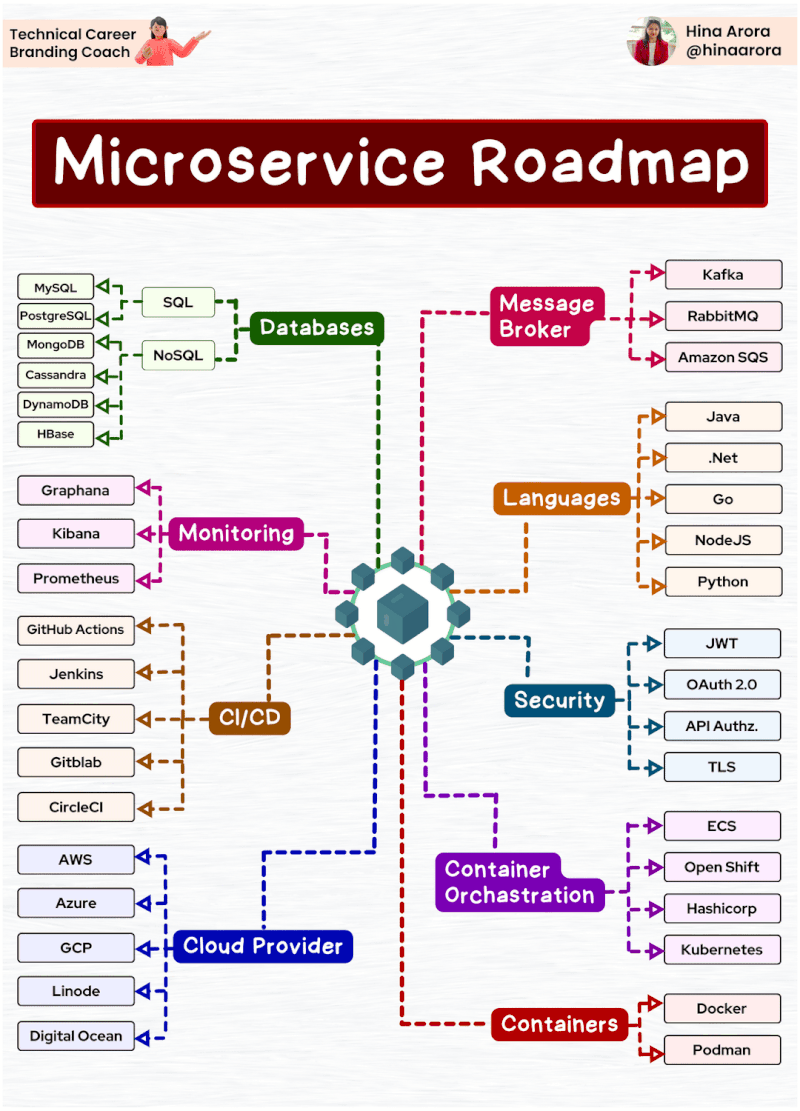
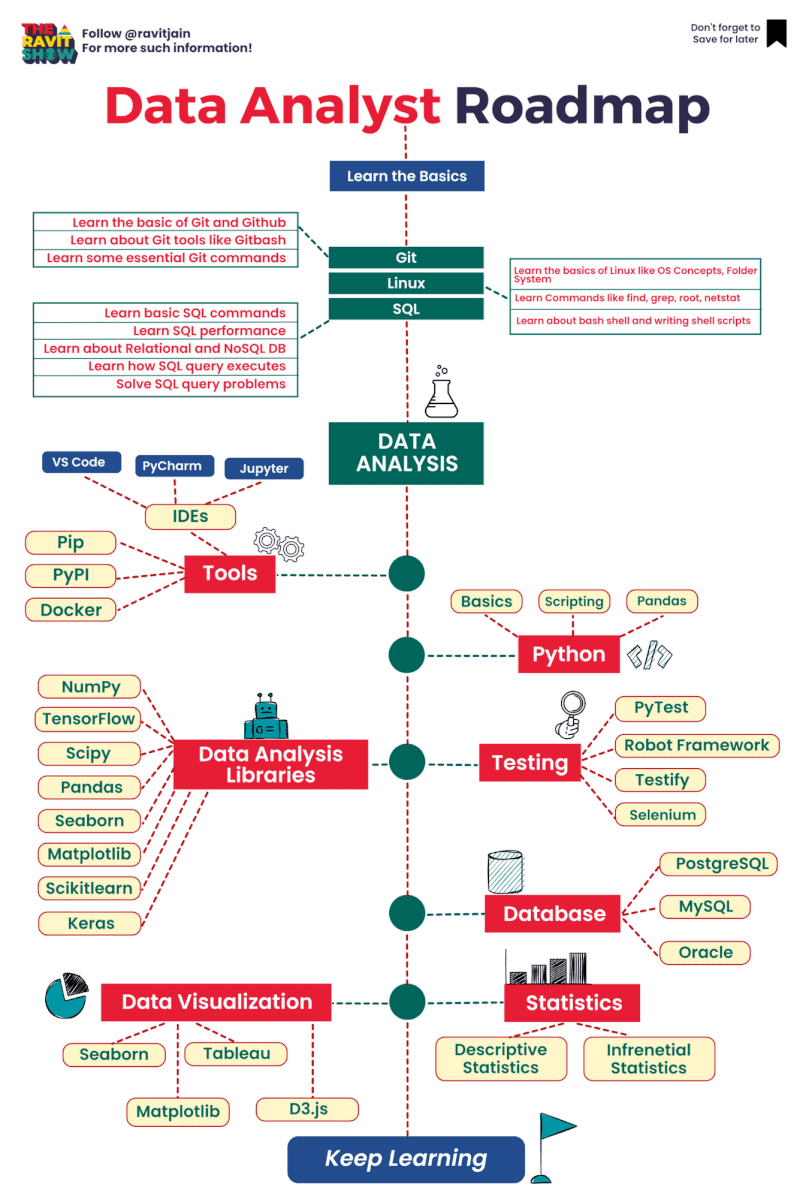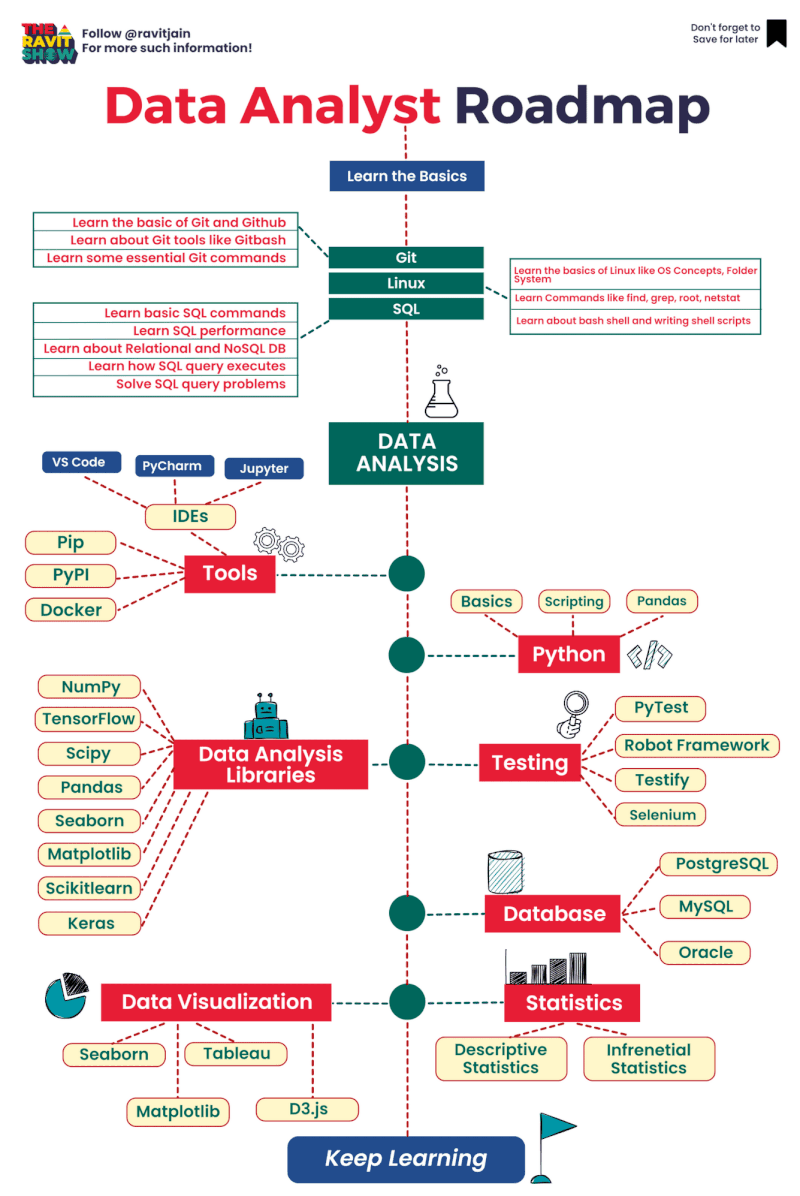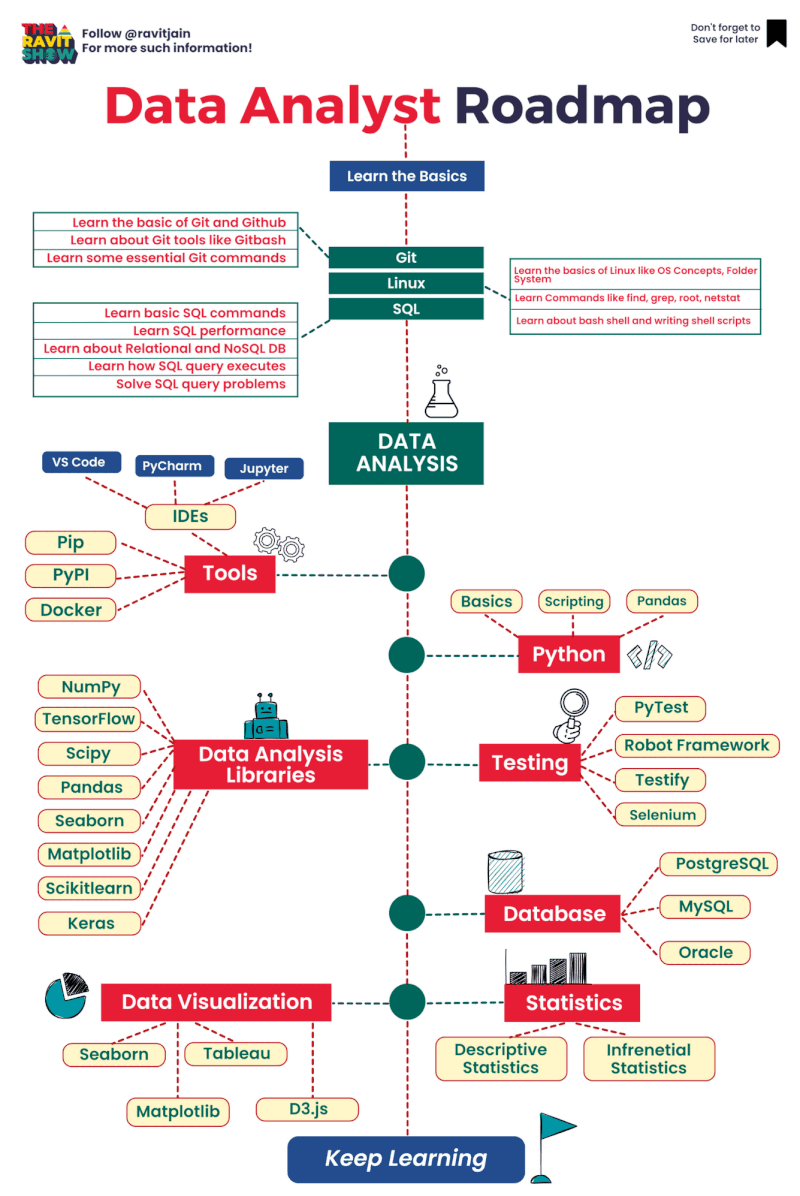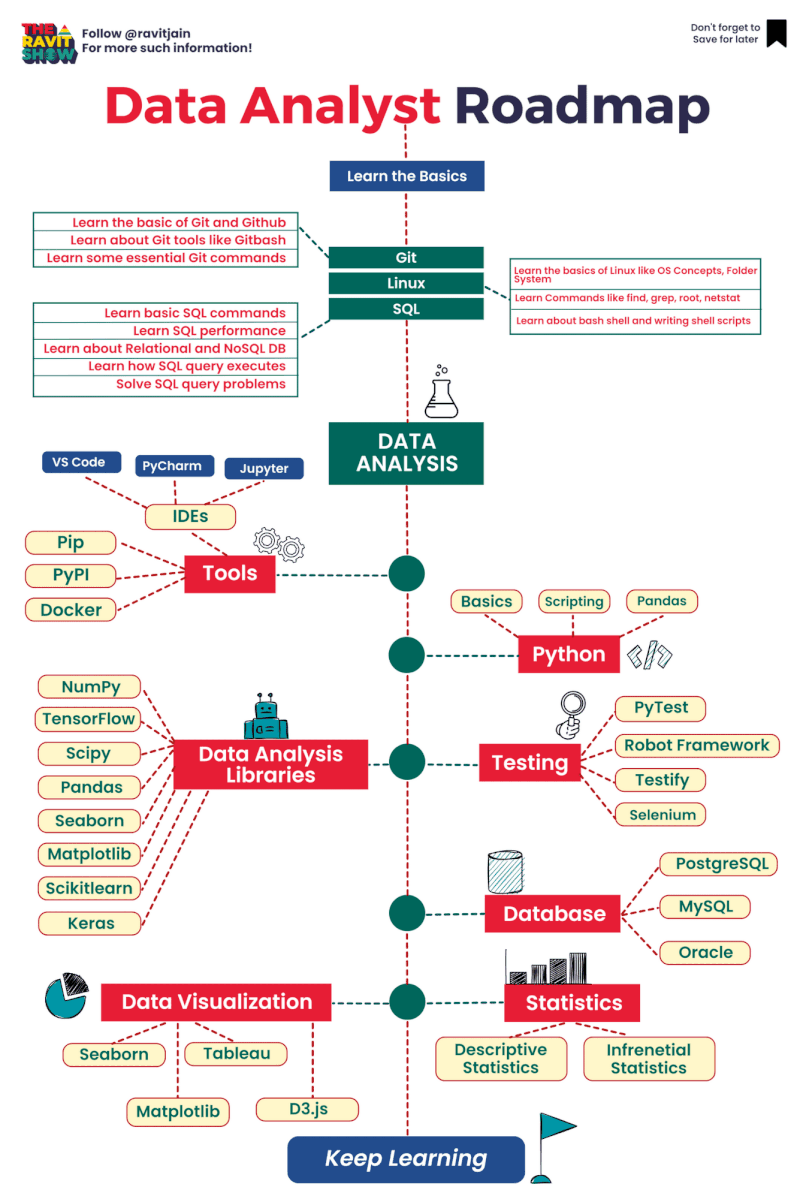
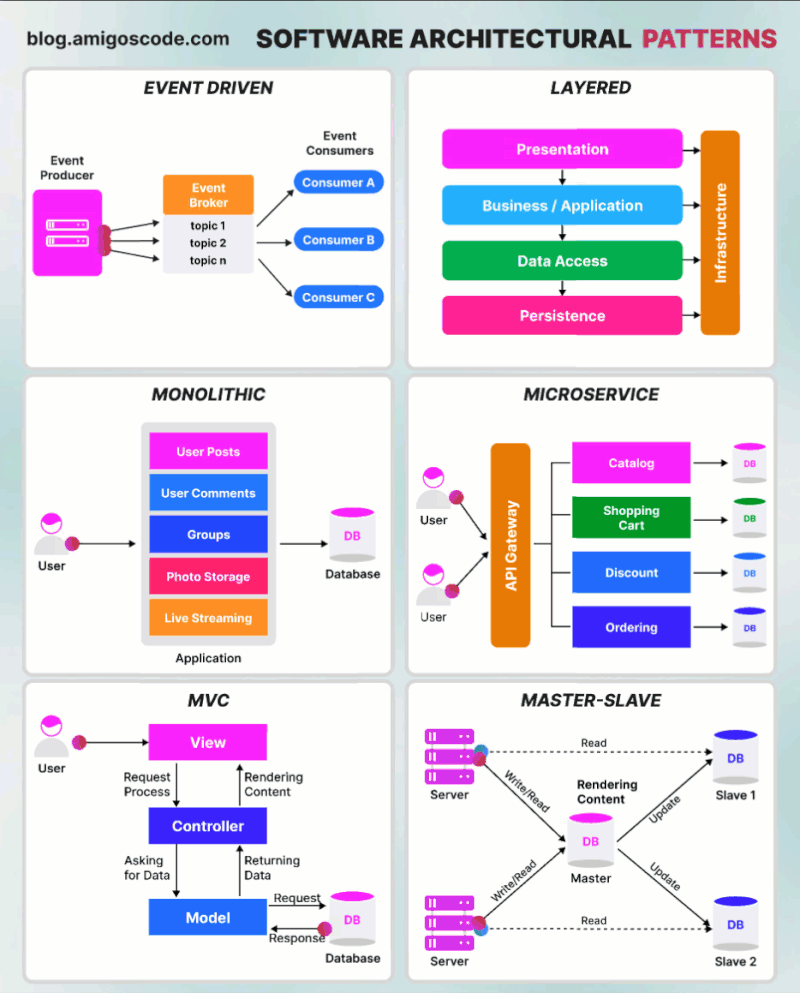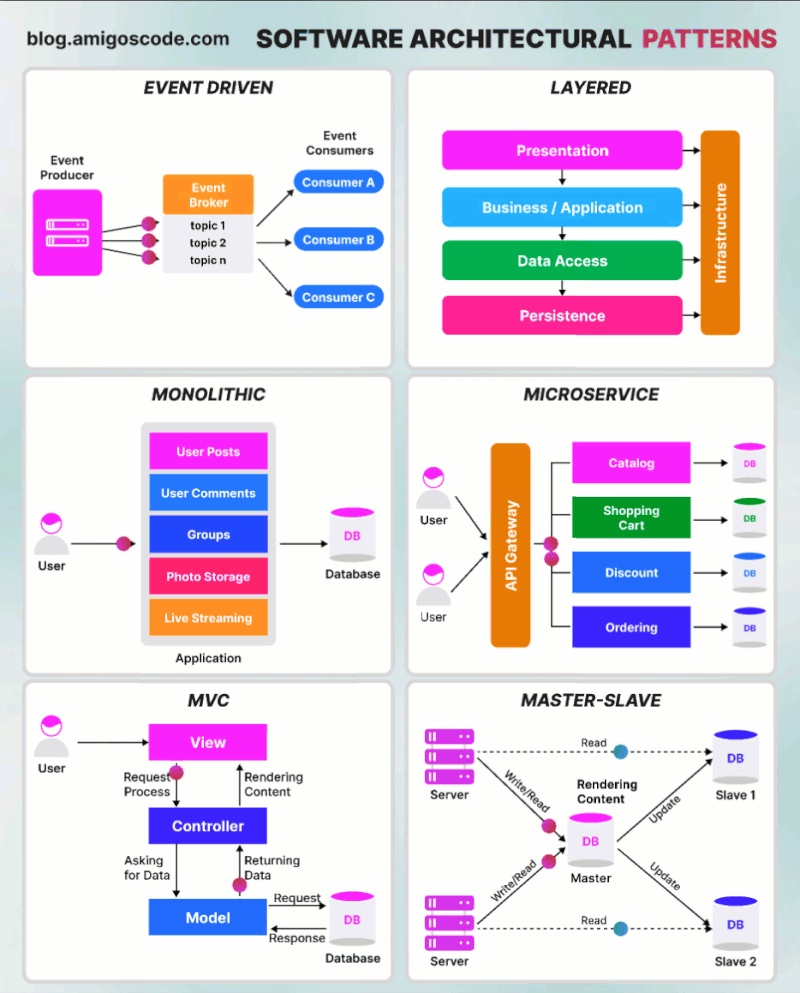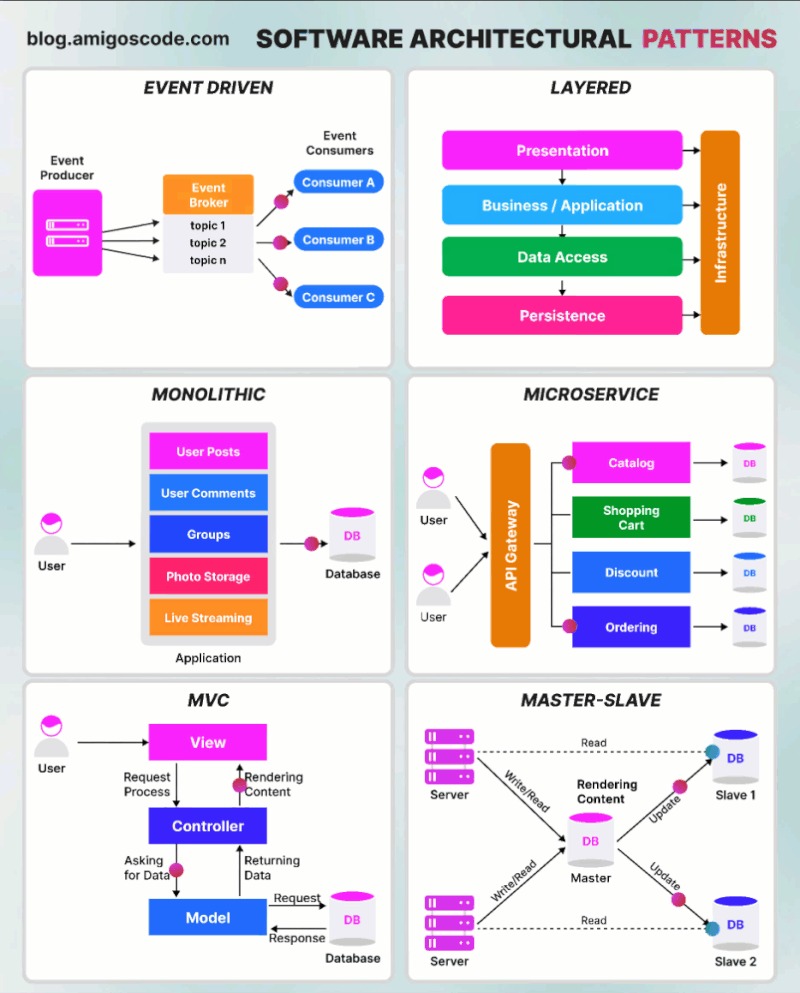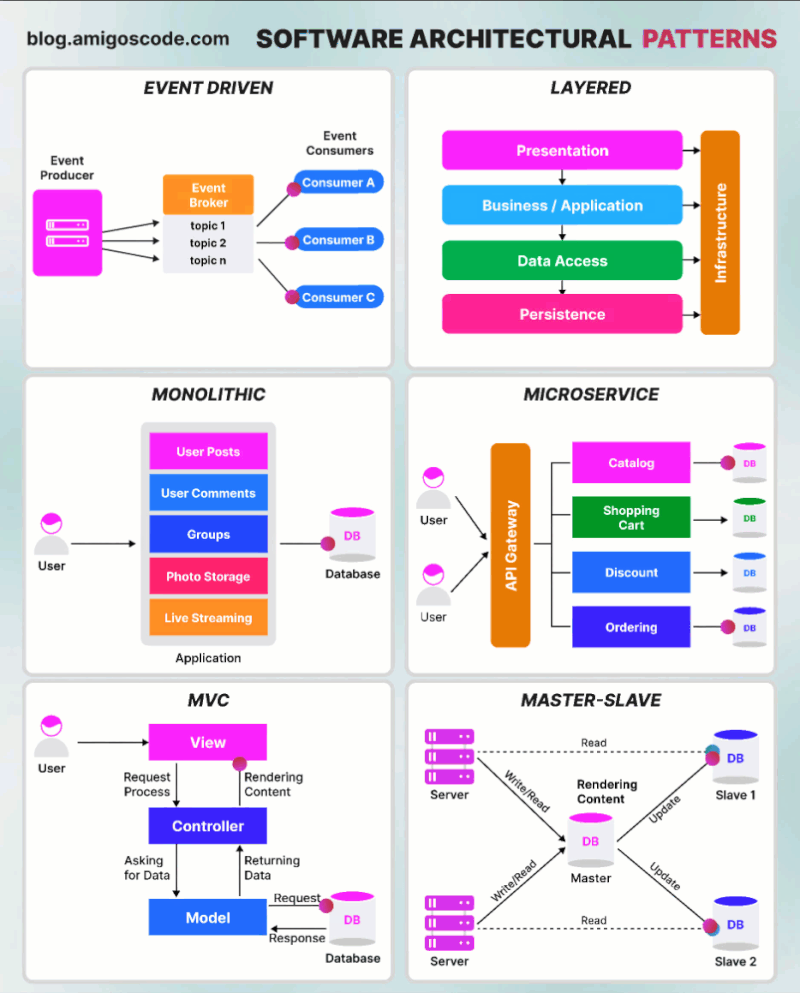
Tìm hiểu một vài AWS SG – Some best practices
Table of contents
SG rule:
- Rules don’t deny access, they permit access based on ports and protocols
- Depending on the type, you may associate several groups to one instance, which the EC2 will treat effectively as a single ruleset.
- You can change security group rules anytime. The EC2 will automatically implement them to the associated instances.
- If there are several rules for one port, the AWS applies the most permissive or weakest rule. For example, if you have a rule that allows access to TCP port 22 (SSH) from IP address 203.0.113.1, and another rule that allows access to TCP port 22 from everyone, everyone has access to TCP port 22.
Some best practices:
- Restrict outbound traffic to specific destinations or ports. This ensures that the cloud data doesn’t go anywhere they aren’t supposed to be.
- Prevent inbound traffic from 0.0.0.0/0, which allows any IP address to be a source. This makes your data more vulnerable to hacking, DDoS attacks, and other threats that may enter the cloud.
- Enable flow logging on your cloud. This allows you to track all traffic going in and out of each instance. You’ll also be able to check for security groups that need their rules changed, such as those that permit access from unknown IP addresses.
- Limit access to ports 445 and 20/21 to authorized parties only. Port 445, which is usually for Common Internet File System or CIFS protocol use, can allow outsiders to access your data through the internet. Likewise, ports 20/21 are often used for File Transfer Protocol or FTP, which lets users download files online.
Reference: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/security-group-rules.html
Bạn thấy bài viết này như thế nào?