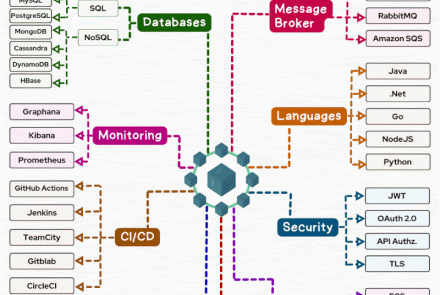
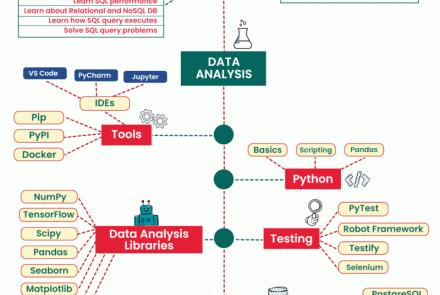
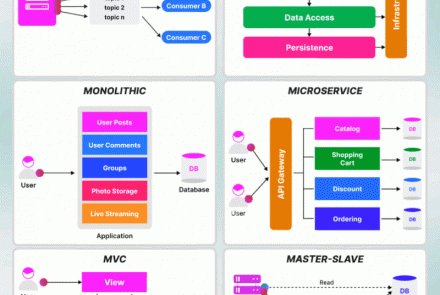
Ethical Hacking and Countermeasures (Module 11 -- 20)
Table of contents
Social Engineering
Types of Social Engineering
Behaviors vulnerable to attacks
Social Engineering Threats and Defenses
Countermeasures for Social engineering
Policies and Procedures
Impersonating Orkut, Facebook, and MySpace
Identity Theft
Countermeasures for Identity theft
File đính kèm
Bạn thấy tài liệu phát triển bản thân này như thế nào?